Cyber winds ༄༄
Cybersecurity and infrastructure software trends, supported by 33N ventures
In the aftermath of RSA early this month, always intense in marketing buzz, we took some time reflect on our latest investment in StrikeReady. For those who missed it, 33N Ventures led the company’s $12M Series A round, joined by Hitachi Ventures, Monta Vista Capital, and industry luminaries Brian NeSmith and Rod Beckstrom. More details here.
The investment comes on a fundamental belief in StrikeReady’s tech edge. In very short terms, StrikeReady's ontology and processing engines form the logic backbone for attack and knowledge harvesting, data analysis, and contextualisation, creating customer-specific threat modeling. On top of this backbone, StrikeReady then leverages its integrations with hundreds of security tools and intelligence feeds to support diverse use cases such as alert management, security analytics, and threat intelligence, and can operate in self-assist, semi-assist, or fully autonomous modes.
Marketing buzz aside, we believe in true tech. But let’s jump right in to understand more.
First-row seat to the Problem
Our team has had its fair share of investment and operational experience across the MDR and MSSP segments having backed successful firms such as Arctic Wolf, European S21sec or Excellium. After 10+ years of deploying, managing and testing a myriad of SOC vendors across Europe and the US, we’ve seen first-hand the challenges that security teams face in terms of response efficacy, scalability, cost management and operational resiliency. From SIEM to SOAR or TIP, we’ve closely followed the waves of innovation that have attempted to address these challenges; yet, despite some great tech advancements, the same concerns remain top-of-mind for CISOs year in and year out.
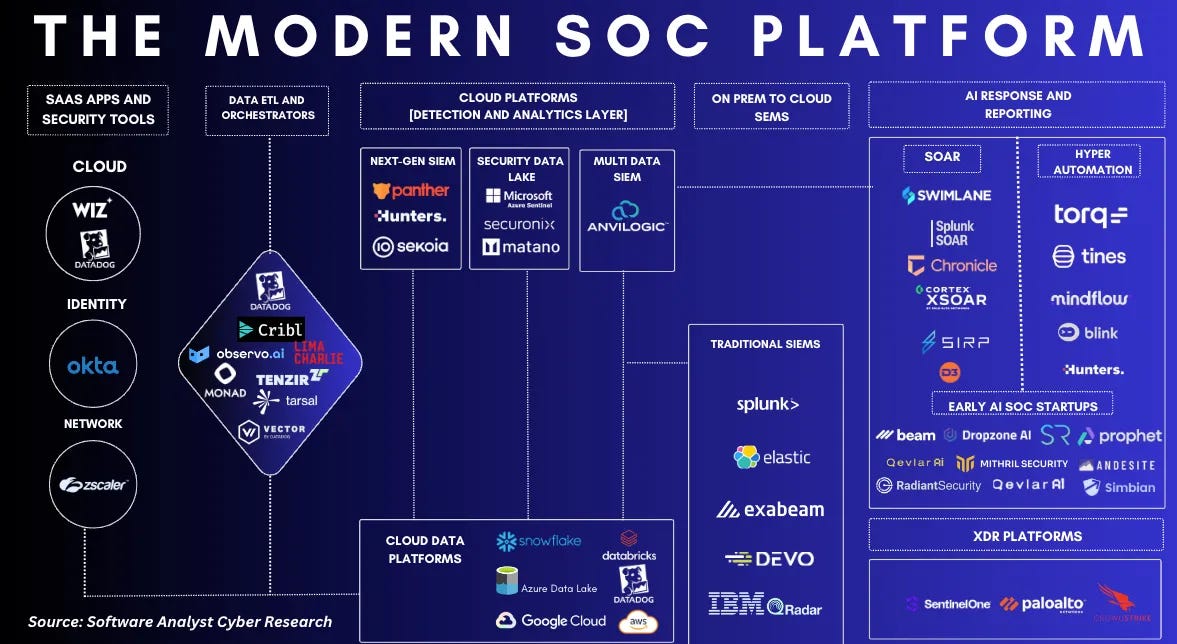
We’ll focus here on how the emerging developments in SOC automation can help address these challenges of efficiency, effectiveness and scale. For a broader view of all moving pieces around modern SOC platforms, we encourage you to read this post (from which we pulled the graphic below).
The evolution of SOC automation
As the post above depicts, from bespoke automation scripts, to SOAR platforms, to no/low-code workflow management tools, “SOC teams have been approaching automation in different ways depending on budget, technical talent and team size.”
SOAR tools were the first to burst into the scene to address the need for better SOC automation and were positioned as extensions of traditional SIEMs. This was a first attempt to bring automation into incident handling and the early pioneers were rewarded with high acquisition prices, if not market penetration (see Palo Alto/Demisto, Sumo Logic/DF Labs, Google/Siemplify, for example). These SOAR platforms suffered from the same pains of their counterparts (SIEMs or even UEBA tools), namely of being too complex and costly to deploy and maintain and, most challenging of all, require a senior analyst to operate them. TCO quickly becomes prohibitive especially if we factor in-house engineering talent and professional services needed to implement and operate such tools. We had first-hand experience with SOAR tools having implemented them across our former MSSP Group so could quickly relate to the pain of onboarding these tools.
Low-code workflow management tools (or hyperautomation) came to market recently with the aim to removing the complexity of SOAR by providing an intuitive, drag-and-drop interface for workflow automation, while still allowing the most talented analysts to customise pipelines at the command line. These tools have experienced a lot of market hype recently, but some questions still remain as to how effectively these tools will scale to handle increasingly more complex attack vectors, use cases, and technology integrations. On the flip side, these vendors can be applicable to use cases beyond security, for instance into IT, fraud, or application development.
More recently, vendors have been researching ways to leverage AI/GenAI advancements, and ultimately continue the trajectory of higher automation and better analyst experience. Microsoft Security Copilot and Crowdstrike Charlotte AI are some attempts to create analyst’s virtual assistants. By taking advantage of massive data lakes and recent partnerships with foundational models, cloud providers are using LLMs to understand log data and query it based on security professional’s prompts. Although facing initial experiments, this technology is expected to have a significant impact on a multi-billion-dollar category.
Why StrikeReady
Understanding some of the low-touch AI applications that evaded the market, we have tried during our assessment of various SOC platform technologies to separate the conversational assistant from the core back-end stack. During our interactions with StrikeReady, it became evident that the company had developed a balanced vision centralising and integrating essential security operational domains into a unified, integrated one-stop-shop solution.
Throughout our assessment, the technology rated superior across several themes. Its ontology and processing engines create the logic backbone for attack and knowledge harvesting, action invocation, as well as data retrieval, analysis, and contextualization. Its systems organize all data ingested from customer’s existing stack, creating relationships between identities, assets, vulnerabilities, incidents, and threats, to ultimately build a specific threat model per customer. By having hundreds of bi-directional integrations, not only pulling data, but owning workflows, triggers, and pushing actions, the platform is set to cover a multitude of use cases such as alert and case management, security analytics, threat intel operationalisation, red team exercises, vulnerability prioritisation, among others. Ultimately, response to users can be triggered using different operation modes: self-assist, semi-assist or full autonomous.
On top of a great product, there was the team’s vision and passion to accomplish something meaningful in this space. Yasir’s leadership and track record of leading multiple R&D initiatives around FireEye’s multi-product portfolio and team’s long-standing relationship reinforced our confidence and sealed the deal.
Onwards and upwards
It’s been a pleasure working with this team and we can’t wait to see how we can contribute to the industry’s pursuit of increased analyst productivity and wellbeing.
In case you’re interested to know more, please check www.strikeready.com.